<< Previous << [Session1 Index] >> Next >>

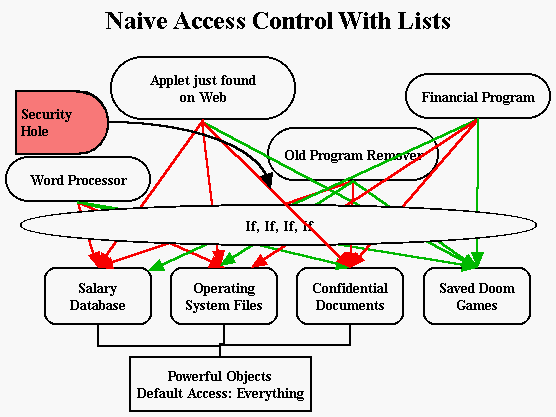
As noted earlier, naive security thinking leads to attempts at security using access control lists. This requires a million slow, clumsy "if" statements, with constant checking to see if the next operation is allowed for the user. Missing just one place where a test is required leaves a security hole. Putting the test in every possible place where it might be needed leaves a performance catastrophe.
The solution comes from quite the opposite direction: Do not start out with a wide-open system and do checks for security-legal operations. Rather, start with an empty system and add legal operations one at a time. Operations that are not secure are simply invalid--either the operation doesn't make sense, or, better yet, the operation cannot even be requested. This approach is known as Capabilities Based Security. As we explore the nature of Capabilities Based security, we will look at several examples of how capabilities can replace the mountain of "if" statements.