<< Previous <<
[Session1 Index]
>> Next
>>
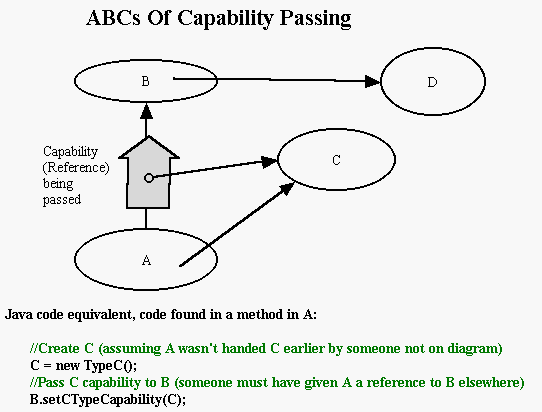
There are only 2 ways to acquire the object C: Create C yourself, or
be handed a pointer to C by someone else.For A to hand B a pointer to C,
A must have a pointer to C, and a pointer to B. Because A has the choice
of whether to hand B the capability on C, this is discretionary
security. Because A must have a pointer to B to hand him the capability,
this is known as mandatory security. One of the interesting
characteristics of this arrangement is that capabilities cannot be
forged: if you have the reference to the object you have the capability
so you don't need forgery, while if you don't have the reference, you don't
have enough information to create a forgery.
Meanwhile, take a look at the security surrounding D. B can service requests
from A using D without exposing D to A. As such we would say that D is
encapsulated by B.

